If you are interested in registering for RISC-V Day Tokyo 2024 on January 16, 2024, click here.
Codasip has made significant advances in RISC-V processor technology. Recently they announced a new series of RISC-V processors called the 700 family. The series is a highly configurable family of processors designed for custom compute applications, allowing you to balance performance, power, and area in your specific design. This allows each core to be optimized for specific use cases using Codasip Studio™.
Additionally, Codasip announced the first commercial implementation of CHERI, an advanced security mechanism to proactively prevent cyber-attacks. This technology enables the creation of products with security built-in by design, allowing businesses to take proactive security measures.
These Codasip advances address the need for customizable, high-performance computing solutions as the technology industry rapidly evolves. With innovations like these, Codasip is accelerating the adoption of RISC-V across a variety of industries.
If you are interested in learning more about these latest developments and how they will impact the future of semiconductor technology, we highly recommend attending the RISC-V conference. Codasip’s participation at the conference is a great opportunity to gain insight into the next generation of the RISC-V processor family, their commercial applications, and how they are shaping the custom compute performance landscape.
CHERI (Capability Hardware Enhanced RISC Instructions) is a technology developed by researchers at the University of Cambridge. It is designed to enhance the security of computer systems by extending the traditional hardware instruction set. CHERI’s purpose is to prevent common security vulnerabilities commonly found in modern computing systems, such as buffer overflows and memory corruption attacks.
The main feature of CHERI is the introduction of Capabilities, which are extension pointers with built-in protection. These features control access to memory and ensure that only authorized code and data can access specific memory areas. This mechanism significantly reduces the risk of many types of cyber attacks.
By integrating CHERI technology into processors, it is possible to create systems that are inherently more secure against many common exploits, such as processors based on the RISC-V architecture. This technology is especially relevant in today’s world, where cybersecurity threats are becoming increasingly sophisticated and pervasive.
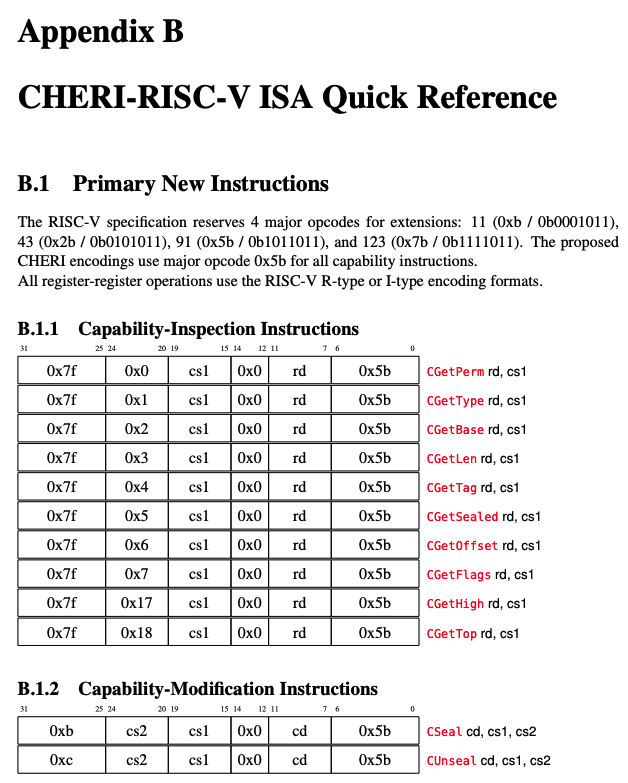
Below is the beginning of the CHERI extended instruction set described in the paper.
The concept of Capability Hardware Memory Protection (CHMP) is old and has been studied in computing for quite some time. It dates back to the early days of computer science and was originally developed as a way to increase the security of computer systems and manage access control. CHMP involves the use of features that are tokens or keys that provide access to memory locations. These features allow you to control and restrict how memory is accessed by different parts of your program and by different users, increasing security and preventing unauthorized access. Although the idea is historic, its implementation and relevance have evolved with advances in computer technology, especially in the context of increasing security threats in the digital age.
Capabilities Hardware Memory Protection (CHMP) and CHERI (Capabilities Hardware Enhancements RISC Instructions) are related but distinct concepts in computer security.
CHMP – Hardware Memory Protection Feature:
General Concepts: CHMP is a broad concept that includes the use of features for memory protection. A capability in this context is a token or key that grants specific access to a memory location.
Purpose: The primary purpose of CHMP is to manage and control access to various memory segments, prevent unauthorized access, and enhance security.
Implementation: CHMP can be implemented in different ways depending on the system architecture and requirements. This is a common approach to memory protection that can be found in many different forms in computer systems.
CHERI – Functional Hardware Enhancement RISC Instructions:
Specific implementation: CHERI is a specific implementation developed by the University of Cambridge that extends the traditional hardware instruction set with functionality.
Advanced features: CHERI introduces features directly into the processor architecture, providing fine-grained memory protection and increased security against common vulnerabilities such as buffer overflows.
Integration with RISC architectures: CHERI is particularly notable for its integration with RISC (Reduced Instruction Set Computer) architectures, which provides a way to create more secure systems without significantly impacting performance.
In summary, while CHMP is a general concept for using memory protection features, CHERI is a specific implementation that integrates this concept directly into processor architectures, especially RISC systems. CHERI represents a modern approach that applies CHMP principles in a way that addresses modern security challenges.

